Accessing restricted blob storage from virtual networks and Azure CDN
I decided to isolate Azure storage account behind this blog due to growing number of attacks against this little nice reading corner. I have anyway Azure CDN service enabled and it is perfect tool to get all static content of this blog as close to my dear readers as possible. Azure storage can be expensive and this is why I don’t want unbuffered traffic to land there, specially if it is generated by bunch of bots that doesn’t commit to glory of this blog anyhow. Here’s how to restrict public access to Azure storage account but keeping blob storage open for virtual machines and other Azure services.
What we want to achieve
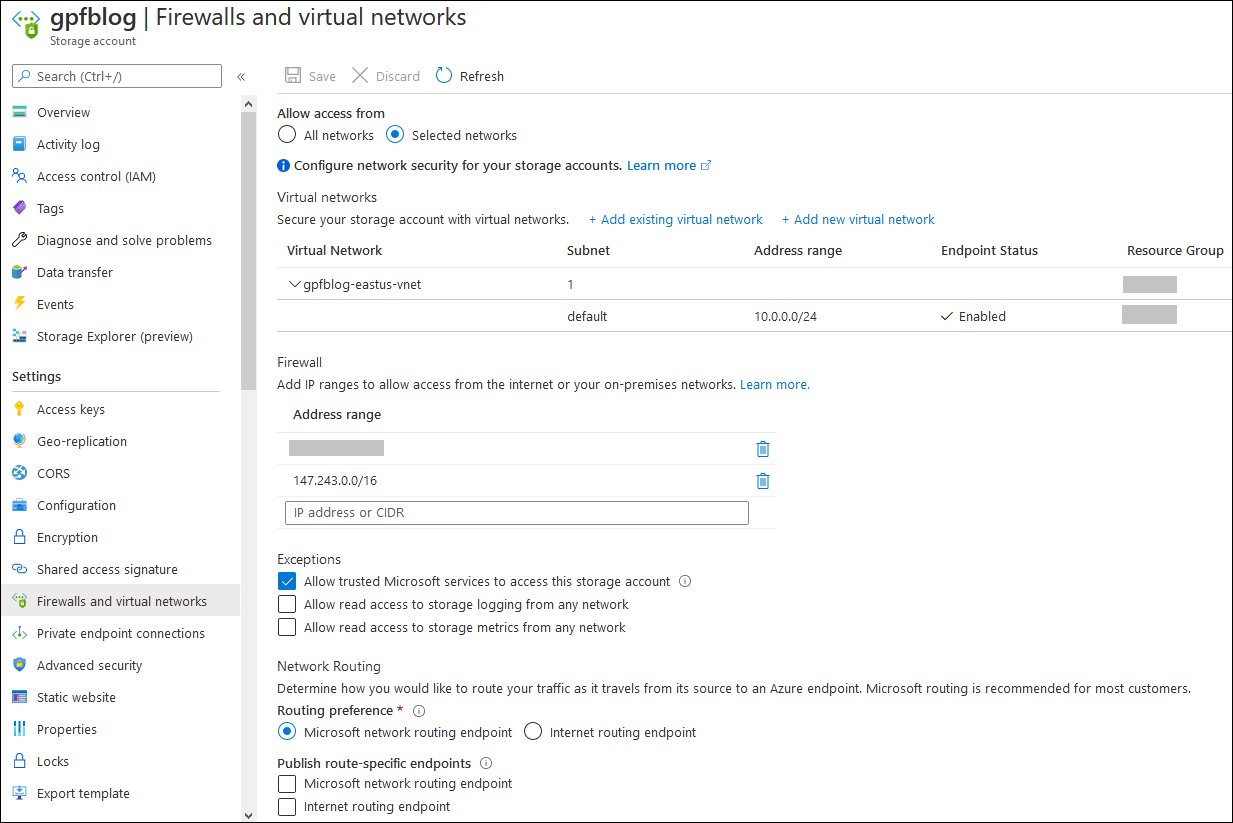
Here’s the simple overview of architecture components involved to blob storage topic. On this diagram components are connected the way I want it to be finally.
Publisher must have direct access to blob storage from specified static IP. Backend machines must also be able to access blob storage as they publish newly combined and minified CSS and JS files to blob storage automatically. It’s clear that Azure CDN must be able to access blob storage. The last accessor is blog reader from public internet. Readers access static content only through Azure CDN.
Virtual network for virtual machines
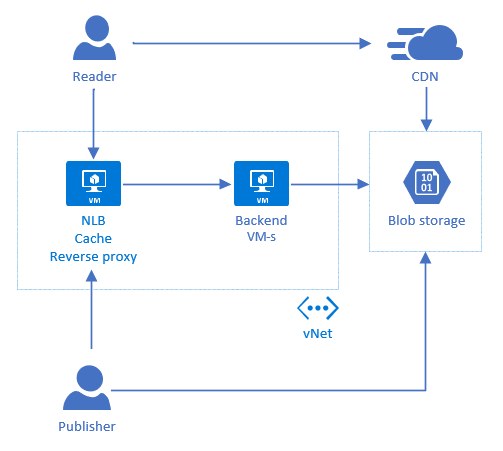
As my blog is hosted on virtual machines (VM) then I have virtual network where all these VM-s belong. One of them is directly visible to public internet while others are not directly accessible.
If I restrict access to blob storage then somehow VM-s must still have access to it and for this we need service endpoint to blob storage. This will be the link between vnet and blob storage.
Configuring storage account
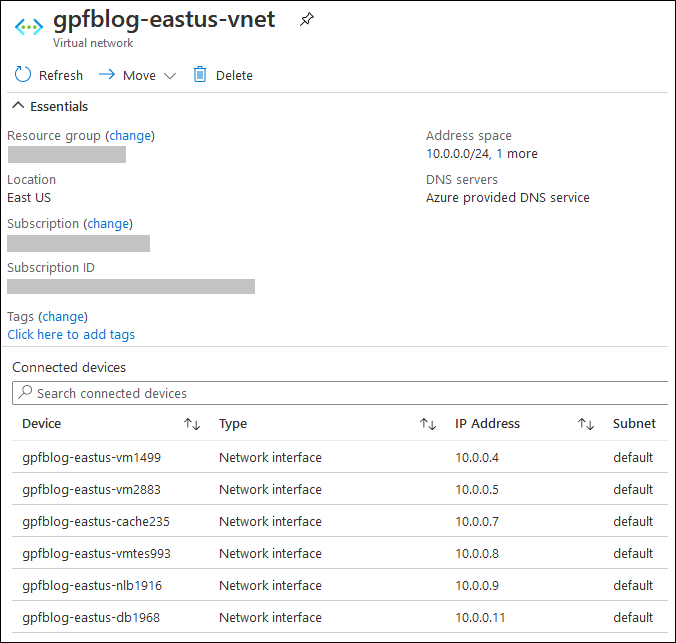
The easiest way to restrict access to blob storage and create service endpoint at same time is to configure storage account. With just few moves we will get all settings in place.
Here are the steps I did:
- Open storage account settings in Azure portal
- Move to Firewalls and virtual networks section
- Allow access from selected networks only
- Select your vnet and let Azure to add service end-point there for blob storage
- To firewall address ranges add the IP-s you use to access blob storage (static IP in office or home)
- Important! Add address range of Azure CDN service: 147.243.0.0/16
- Make sure you have selected checkbox “Allow trusted Microsoft services to access this storage account”
- Leave all other settings like they are and click Save.
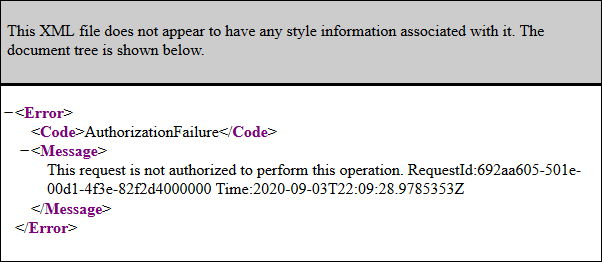
The whole process takes few minutes of time and I faced no single issue. When file is directly requested from blob storage then the result is XML with error information.
Wrapping up
It’s great how I can control and configure services on Azure I use to host this blog. Keeping expenses under control by restricting access to blob storage may come with some small financial wins. But more important is to avoid mistakes like allowing blog to generate direct links to blob storage when Azure CDN is there to take all static content as close to reader as possible. I’m even more suspicious on aggressive bots that are trying to index things too frequently and therefore generate big amount of storage transactions.